
Wi-Fi is a family of radio technologies commonly used for wireless local area networking (WLAN) of devices. Wi‑Fi is a trademark of the Wi-Fi Alliance, which restricts the use of the term Wi-Fi Certified to products that successfully complete interoperability certification testing.
Wi-Fi uses the IEEE 802.11 networking standards, which come in several types:
The radio signal used for Wi-Fi communication is very similar to the radios used for cell phones and other devices. The signal is transmitted and received with encoded digital data. Wi-Fi transmits at frequencies of 2.4 GHz or 5 GHz. The higher frequency allows the signal to carry more data.
- 802.11a transmits at 5 GHz and can move up to 54 megabits of data per second. It also uses orthogonal frequency-division multiplexing (OFDM), a more efficient coding technique that splits that radio signal into several sub-signals before they reach a receiver. This greatly reduces interference.
- 802.11b is the slowest and least expensive standard. For a while, its cost made it popular, but now it’s becoming less common as faster standards become less expensive. 802.11b transmits in the 2.4 GHz frequency band of the radio spectrum. It can handle up to 11 megabits of data per second
- 802.11g transmits at 2.4 GHz like 802.11b, but it’s a lot faster — it can handle up to 54 megabits of data per second. 802.11g is faster because it uses the same OFDM coding as 802.11a.
- 802.11n is a widely available standard and is backward compatible with a, b and g. It significantly improved speed and range over its predecessors. For instance, although 802.11g theoretically moves 54 megabits of data per second, it only achieves real-world speeds of about 24 megabits of data per second because of network congestion. 802.11n, however, reportedly can achieve speeds as high as 140 megabits per second. 802.11n can transmit up to four streams of data, each at a maximum of 150 megabits per second, but most routers only allow for two or three streams.
- 802.11ac is backward compatible with 802.11n , with n on the 2.4 GHz band and ac on the 5 GHz band. It is less prone to interference and far faster than its predecessors, pushing a maximum of 450 megabits per second on a single stream, although real-world speeds may be lower.
- IEEE 802.11ax, is one of the two Wi–Fi specifications standards of IEEE 802.11 expecting full deployment in late 2019; the other is IEEE 802.11ay. They can be thought of as High Efficiency Wireless.

In 2018, the Wi-Fi alliance standardized generational numbering so that equipment can indicate that it supports Wi-Fi 4 (if the equipment supports 802.11n), Wi-Fi 5 (802.11ac) and Wi-Fi 6 (802.11ax). These generations have a high degree of backward compatibility with previous versions.
2.4 Ghz versus 5.0 Ghz Band Explained
Building a Wi-Fi network

If you already have several computers networked in your home, you can create a wireless network with a wireless router. This is the multi-functional unit usually supplied by your Internet Service Provider . The unit contains:
- A port to connect to your cable or VDSL modem
- A router
- An Ethernet switch
- A firewall
- A wireless access point
Most wireless routers provide coverage for about 30 meters in all directions, although walls and doors can block the signal reducing the signal strength. If your home is very large, you can buy inexpensive range extenders to increase the coverage.
Once you plug in your router, it should start working at its default settings. Most routers let you use a Web interface to change your settings. You can select:
- The name of the network, known as its service set identifier (SSID) — The default setting is usually the manufacturer’s name.
- The channel that the router uses — Most routers use channel 6 by default. If you live in an apartment and your neighbors are also using channel 6, you may experience interference. Switching to a different channel should eliminate the problem.
- Your router’s security options — Many routers use a standard, publicly available sign-on, so it’s a good idea to set your own username and password.
Security is an important part of a home wireless network. It is important to make sure your security precautions are current. The Wired Equivalency Privacy (WEP) security measure was once the standard for WAN security. The idea behind WEP was to create a wireless security platform that would make any wireless network as secure as a traditional wired network. But hackers discovered vulnerabilities in the WEP approach, and today it’s easy to find applications and programs that can compromise a WAN running WEP security. It was succeeded by the first version of WiFi Protected Access (WPA), which uses Temporal Key Integrity Protocol (TKIP) encryption and is a step up from WEP, but is also no longer considered secure.
To keep your network private, you can use one or both of the following methods:
- WiFi Protected Access version 3 (WPA3) is the successor to WEP and WPA2, and is now the recommended security standard for WiFi networks. It uses either TKIP or Advanced Encryption Standard (AES) encryption, depending upon what you choose at setup. AES is considered the most secure. As with WEP and the initial WPA, WPA3 security involves signing on with a password. Public hotspots are either open or use any of the available security protocols, including WEP, so use caution when connecting away from home. WiFi Protected Setup (WPS), a feature that ties a hard-coded PIN to the router and makes setup easier, apparently creates a vulnerability that can be exploited by hackers, so you may want to turn off WPS if possible, or look into routers that do not have the feature.
- Media Access Control (MAC) address filtering is a little different from WEP, WPA2 or WPA3. It doesn’t use a password to authenticate users — it uses a computer’s physical hardware. Each computer has its own unique MAC address. MAC address filtering allows only machines with specific MAC addresses to access the network. You must specify which addresses are allowed when you set up your router. If you buy a new computer or if visitors to your home want to use your network, you’ll need to add the new machines’ MAC addresses to the list of approved addresses. The system isn’t foolproof. A clever hacker can spoof a MAC address. Spoofing is copying a known MAC address to fool the network that the computer he or she is using belongs on the network.
Wi-Fi Security
Wi-Fi Mesh networks
You have a computer network with the latest Wi-Fi hardware and a 100 Mbps Internet connection. But for some reason, you are suffering from buffering when you try to stream video in the main area. You have called your Internet Service Provider (ISP) and everything seems fine, so what is wrong. Generally the issue is with the Wi-Fi. It is not set up efficiently for a mesh Wi-Fi system.
Cyber Security
Cyber security refers to the technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access.
Most people and business owners don’t have much time to spend on understanding the complexities of the Internet security or establishing complicated responses to potential risks.
Cyber security doesn’t have to be difficult. There are simple measures that if understood and implemented, can significantly avoid, or reduce the impact of, the most common cyber security incidents.
The Cyber Security Guide provides a good over of how to protect yourself from potential attacks.
Practical Activity
Using the supplied Blue network cable network connect your computer to the router as shown in the diagram.
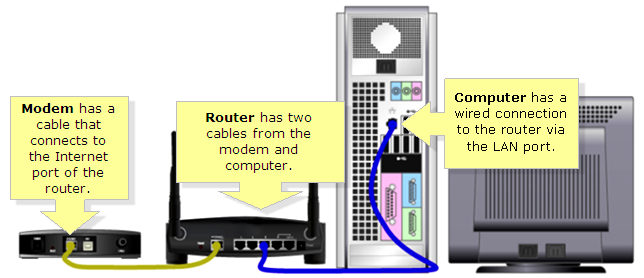
- Ensure you have a valid IP address on the computer. ( Use the ipconfig command to validate).
- Login to the wireless router admin area as shown by instructor.
- List the current clients connected to the wireless router
- Identify the current SSID on the wireless router
- Identify the current security setting for the WLAN.
- Check to see that the 2.4Ghz and 5.0Ghz WLAN are operating.
- Now change the SSID to Classroom#
- Set the security protocol to WPA2 and set the security key for access.
- Now try and connect a wireless device to the WLAN
- Now open web browser and connect to www.google.com
Optional tasks
- Identify the channels set for the WLANs
- Setup a wireless Guest network to operate on the 5Ghz frequency
- Set up the DHCP pool for the WLAN clients.
- Connect a mobile phone to the guest network .
- Identify the phone’s IP address and Gateway Address and MAC Address.
- Now set MAC filtering to only allow known devices
- Use WPS to connect to the WLAN