Session 2 provides an understanding of the functions performed by a modem, switch and router . It introduces the concept of MAC addresses and gives an overview of the TCP/IP protocol in regards to IP addresses.
This session is designed to be delivered in a theory base format with a supportive practical component.
Topics
Open Systems Interconnection (OSI) Model
Theory presentation on the structure and role of the OSI model and how it relates to network architecture. Refer to Network Devices page for OSI overiew.
Modems, Switches and Routers
Video explanation of how each device functions in a network
Modems used in typical NBN Connections
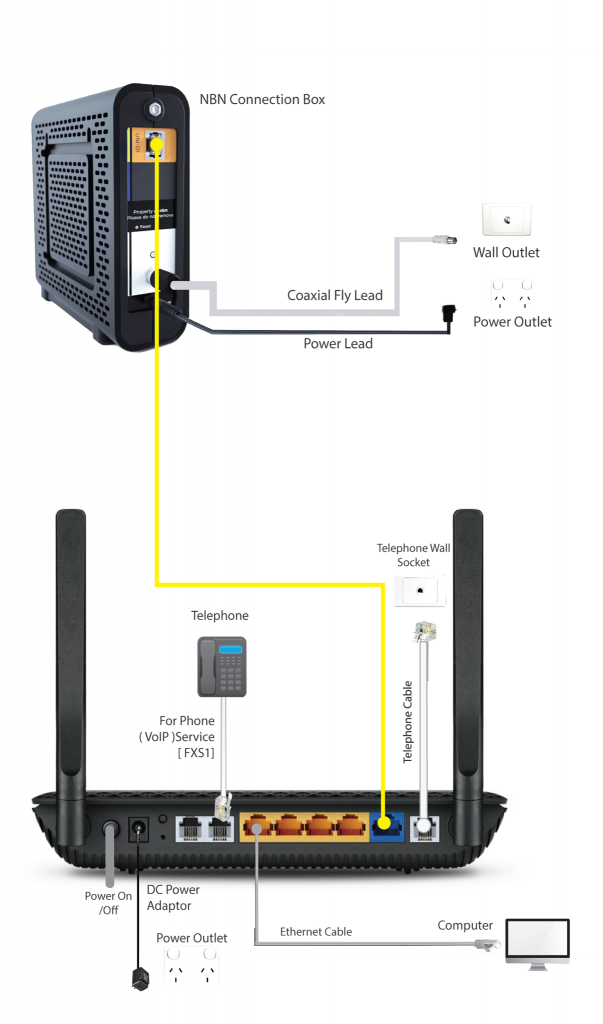
Explanation of now to connect to the NBN using a Hybrid Fibre Coaxial connection.

Explanation of now to connect to the NBN using a Fibre to the Curb connection.

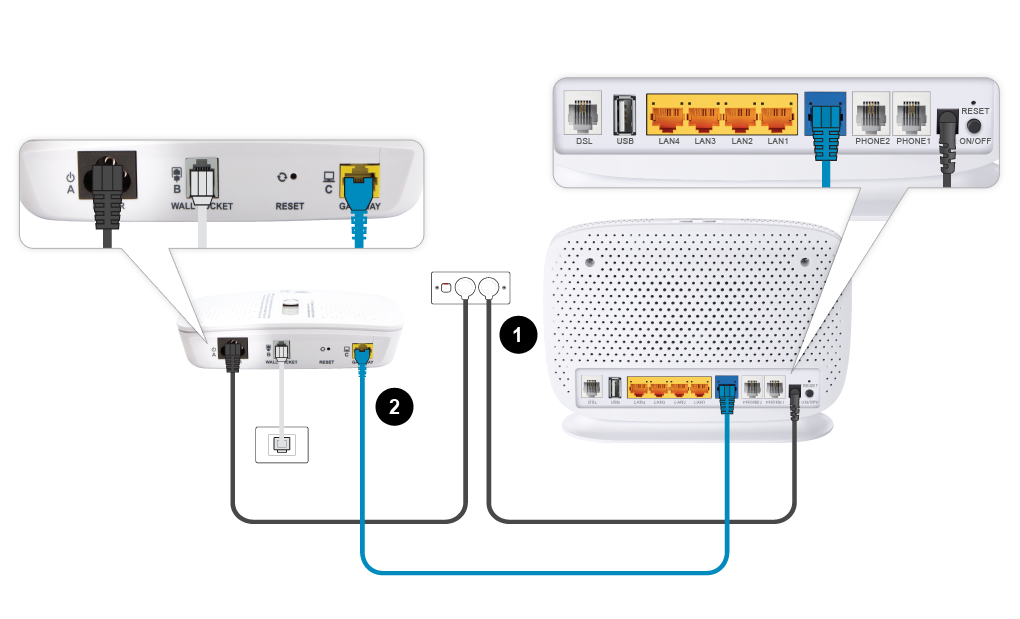
Multi functional devices used in NBN connections
Explanation of now to connect to the NBN using a Fibre to the Node connection.
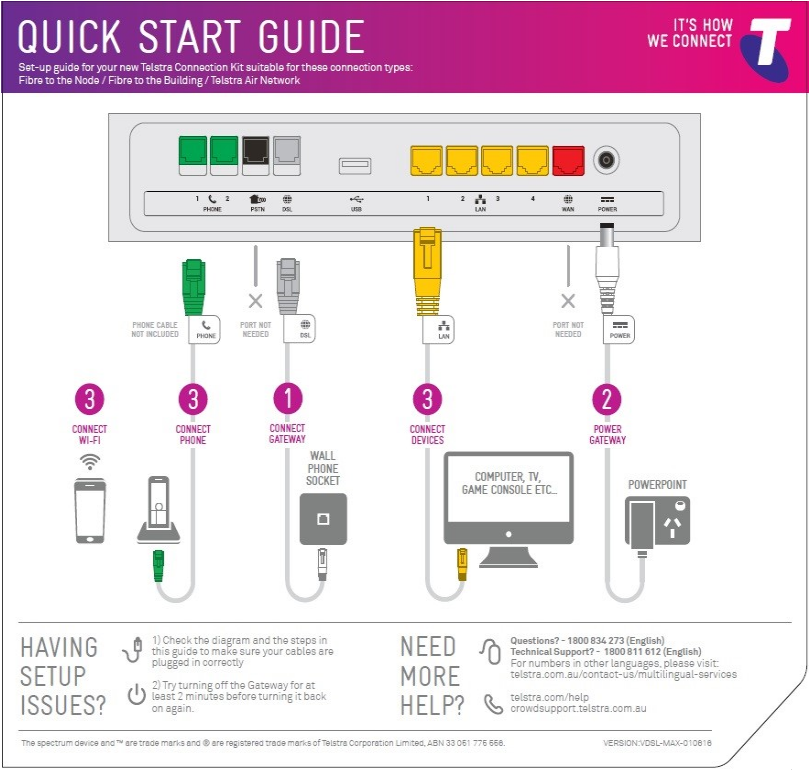
Media Access Control (MAC) Address
The MAC address of a device is a unique 48 bit assigned address assigned to a network interface controller (NIC). For communications within a network segment, it is used as a network address for most network technologies, including Ethernet, Wi-Fi, and Bluetooth. Within the OSI model, the MAC addresses is at the data link layer 2. The MAC address is used by a switch for control the flow of data on the local network.
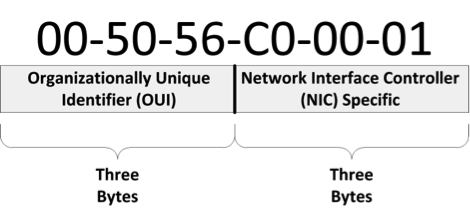
First three bytes are the Vendor ID, The second three bytes are the interface ID
MAC addresses are shown as Hexadecimal numbers from 0 -E. Each number represents 4 binary bits.
(Internet Protocol) IP Address ver. 4
IPv4 uses 32 binary bits to create a single unique address on the network. An IPv4 address is expressed by four numbers separated by dots. Each number is the decimal (base-10) representation for an eight-digit binary (base-2) number, also called an octet.
For example: 192.168.1.1
Available Private Addresses
| Class | Range | Subnet Mask |
| A | 10.0.0.0 – 10.255.255.25 | 255.0.0.0 |
| B | 172.16.0.0 – 172.31.255.255 | 255.255.0.0 |
| C | 192.168.0.0 – 192.168.255.255 | 255.255.255.0 |
Where possible, always use private addressing in your internal network, particularly when the machines getting IP addresses have no chance of ever servicing people’s requests on the Internet.
Default Subnet Masks
A subnet mask is another 4-octet, 32-bit address that “masks” the associated IP address assigned with it. The mask defines the bits that are used for the Network ID and the bits used for the Hosts ID.
For each network class A, B or C, there is a default subnet mask.
- Class A – 255.0.0.0
- Class B – 255.255.0.0
- Class C – 255.255.255.0
Ports
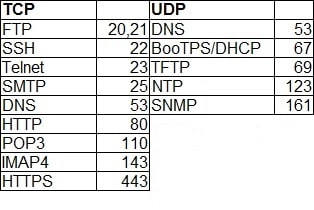
A port is a 16-bit number used to identify specific applications and services. Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) specify the source and destination port numbers in their packet headers and that information, along with the source and destination IP addresses and the transport protocol (TCP or UDP), enables applications running on hosts on a TCP/IP network to communicate.
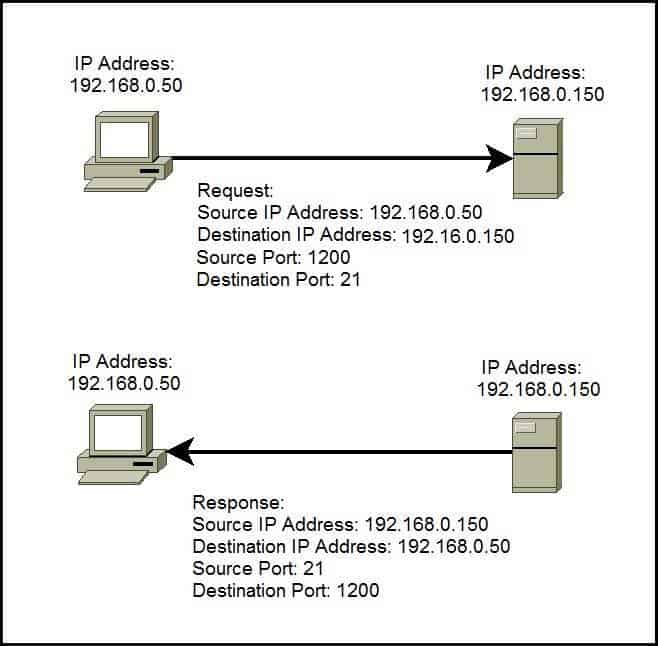
Applications that provide a service such File Transfer Protocol (FTP) and Hypertext Transfer Protocol (HTTP) servers open a port on the local computer and listen for connection requests. A client can request the service by pointing the request to the application’s IP address and port. A client can use any locally unused port number for communication. Consider the following example:
In the picture above you can see that a host with an IP address of 192.168.0.50 wants to communicate with the FTP server. Because FTP servers use, by default, the well-known port 21, the host generates the request and sends it to the FTP server’s IP address and port. The host use the locally unused port of 1200 for communication. The FTP server receives the request, generates the response,and sends it to the host’s IP address and port.
Port numbers are from 0 to 65535. The first 1024 ports are reserved for use by certain privileged services:
NOTE
The combination of an IP address and a port number is called a socket. In our example the web socket would be 192.168.0.50:80.
Practical Activity 1.
Open a command window on your computer.
Windows
Mac
Execute the following commands and document their output.
Practical Activity 2.
Using the supplied ethernet network cable connect your computer to the router as shown in the diagram.
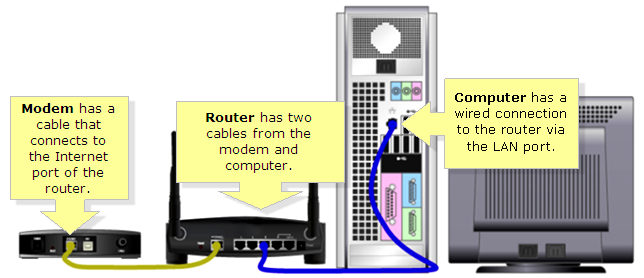
Now complete the following tasks.
- Ensure you have a valid IP address on the computer. ( Use the ipconfig command to validate).
- What is the computer’s MAC Address
- Login to the router as shown by instructor.
- Identify the following on the router LAN port (IP address , Subnet Mask, Gateway)
- Ensure the computer can be seen as a client on the router
- Set the WAN port IP address as shown by instructor.
- Check to see the link light is blinking on the WAN port
- IF WAN port is working OK use the ping command on the computer to ensure connectivity to the Internet.
- Now open web browser and connect to www.google.com
Optional tasks
- Change the DHCP pool to restrict client addresses from 192.168.1.80 – 192.168.1.100
- Setup the wireless network to connect a mobile phone to network.
- Identify the phone’s IP address and MAC Address.